When your B2B prospects overwhelmingly use Microsoft 365 (most enterprise customers do), getting past their spam filters becomes make-or-break for revenue. The mystery junking drives teams to desperation when headers show high SCL and BCL scores while everyone debates “content issues” versus “list quality.”
The answer isn’t some magic bypass trick that compromises security. You need a strategic approach that works with Microsoft’s filtering systems, not against them.
As an email deliverability consultant who has helped hundreds of B2B SaaS companies land consistently in Microsoft 365 inboxes (rather than junk folders), I’ve prepared this comprehensive guide that covers:
- Microsoft 365 spam filtering mechanics and bypass failures
- Safe TABL customer allowlisting versus risky IP bypasses
- Advanced spam filter settings and connection policies
- SCL/BCL header interpretation for delivery diagnosis
- Email warmup for positive engagement patterns
- SPF, DKIM, DMARC authentication setup
Let’s provide you with a clear action plan for improving Microsoft 365 deliverability without compromising security or creating compliance headaches.
Quick solution summary
Don’t have the time to read the entire bit? Skim through this overview:
| Problem | Solution | Implementation time |
| High SCL scores (5-9) | Email warmup plus authentication fixes | 8-12 weeks |
| BCL >= 7 bulk complaints | List validation plus engagement improvement | 2-4 weeks |
| Customer requests IP allowlisting | Provide the TABL allowlisting guide | 1-2 days |
| Authentication failures | SPF/DKIM/DMARC setup across domains | 1-2 weeks |
| Mystery junking | Header analysis plus policy adjustments | 1 week |
If it’s too complicated, we can take care of it for you
Setting up proper Office 365 deliverability requires juggling multiple technical pieces across domains, authentication, and reputation management. If you’d rather focus on your core business while an expert handles your email deliverability, we can take care of everything for you.

EmailWarmup.com offers:
- Dedicated IP address for reputation control
- Pre-send email delivery test and API for monitoring
- Safe customer allowlisting playbooks using TABL
- Unlimited email warmup with 8-12 week reputation building
- Email list validation and automatic replacement (up to 100/month)
- Unlimited deliverability consultations with Microsoft 365 specialists
We can configure your authentication, set up warm-up sequences, and provide your sales team with proper customer allowlisting procedures immediately.
What exactly is Office 365 spam filtering?
Microsoft’s spam filtering system assigns confidence scores that directly impact where your messages land and whether your campaigns succeed or fail.
Exchange Online Protection (EOP) serves as the first line of defense, scanning every inbound message for spam, malware, and phishing attempts.
You can’t completely turn off spam filtering, but you can use Exchange mail flow rules (also known as transport rules) to bypass most spam filtering on incoming messages.
Microsoft uses proprietary algorithms and machine learning models that continuously evolve based on user feedback and threat intelligence.
| Filter component | Function | Impact level |
| SCL scoring | Spam likelihood from -1 to 9 | High |
| BCL rating | Bulk complaint assessment | High |
| Authentication checks | SPF, DKIM, DMARC verification | Critical |
| IP reputation | Connection filtering | Medium |
| Content analysis | Pattern recognition | Medium |
Your sender reputation, authentication status, and content patterns all contribute to the final delivery decision.
How does Microsoft 365 determine spam confidence levels?
Understanding SCL and BCL scores gives you diagnostic power to fix delivery issues instead of relying on guesswork (because guessing is what got you into the junk folder in the first place).
These numerical ratings determine whether your messages reach inboxes or get buried, where most recipients never check.
Spam confidence level breakdown
In all organizations with cloud mailboxes, inbound messages undergo spam filtering and are assigned a spam score.
| SCL Score | Verdict | Action |
| -1 | Bypassed filtering | Inbox delivery |
| 0-1 | Not spam | Inbox delivery |
| 5-6 | Spam | Junk folder |
| 7-9 | High confidence spam | Quarantine |
That score is mapped to an individual spam confidence level (SCL) value, which is added to the message in an X-header.
Bulk complaint level impact
The BCL value gets added to the message in an X-header and works similarly to SCL for identifying messages as spam.
A higher BCL value indicates a bulk message is more likely to exhibit undesirable spam-like behavior (translation — your recipients are hitting that “report spam” button).
| BCL Score | Classification | Typical Action |
| 1-3 | Legitimate bulk | Normal delivery |
| 4-6 | Moderate bulk | May hit junk |
| 7-9 | High complaint risk | Spam treatment |
When your BCL score reaches 7 or higher, Microsoft often converts it to an SCL 6, which triggers spam folder delivery regardless of the quality of your content. You could write Shakespearean prose and still get junked with a high BCL score.
Why do traditional spam filter bypass methods fail?
Many organizations try shortcuts that actually hurt their long-term deliverability (kind of like taking a shortcut through a swamp to avoid getting wet).
IP allowlisting creates security holes
Messages from entries in the allowed senders list or the allowed domains list bypass most email protection (except malware and high-confidence phishing) and email authentication checks.
Entries in the allowed senders list or the allowed domains list create a high risk of attackers successfully delivering email to the Inbox that would otherwise be filtered.
We recommend that you don’t use these features because they may override the verdict that is set by Microsoft 365 spam filters.
When customers add your IP to their allow lists, they’re essentially creating security holes in their defenses (imagine leaving your front door unlocked because you trust one particular delivery driver).
Authentication bypasses backfire
Some services suggest having customers disable SPF or DMARC checks for your domain.
However, Microsoft’s algorithms learn that your domain can’t be trusted to authenticate properly, leading to lower reputation scores over time.
Content-only approaches miss the point
While avoiding “spammy” words helps, modern spam filters focus much more heavily on sender reputation, authentication status, and engagement patterns. You can write perfect content and still land in junk if your reputation signals are wrong.
The sustainable approach involves building genuine trust signals that Microsoft’s algorithms recognize as legitimate business communication.
How can you safely bypass Office 365 spam filtering?
Rather than trying to trick the system (which is like trying to outsmart a computer that processes millions of emails daily), you want to earn legitimate bypass status through proper authentication and reputation building.
Mail flow rules for legitimate scenarios
You can use mail flow rules (also known as transport rules) to affect spam filtering by setting the spam confidence level (SCL) on messages.
Navigate to the Exchange admin center, create a new mail flow rule, and set conditions like specific sender IP ranges. Then select “Modify the message properties” and “set the spam confidence level (SCL)” to “Bypass spam filtering.”
Use these only for legitimate business needs like routing through third-party security services (not as a blanket bypass strategy that compromises security).
Authentication requirements come first
Before implementing any bypass mechanisms, ensure your SPF, DKIM, and DMARC records are properly configured across all sending domains and subdomains.
As of September 2022, allowed senders, domains, or subdomains in your organization’s accepted domains must pass email authentication checks to skip spam filtering.
Reputation building through warmup
The most sustainable bypass method involves slowly increasing sending volume while maintaining high engagement rates (think marathon training, not sprint). Microsoft’s algorithms learn to trust domains that consistently generate positive user interactions over 8-12 week periods.
What’s the proper way to set up customer allowlisting?
When enterprise customers ask, “can you be allowlisted?” you need to provide guidance that enhances their security rather than compromising it. Most customers don’t understand the security implications of different allowlisting methods (they just want their emails to work).
Tenant Allow/Block List implementation
The Tenant Allow/Block List (TABL) offers a secure alternative to risky IP allowlisting. To exempt a sender or domain from threat protection checks, you can utilize the Tenant Allow/Block list from the Microsoft 365 Defender portal.
| Step | Action | Location |
| 1 | Log in tothe portal | Microsoft 365 Defender portal |
| 2 | Navigate to policies | Email & collaboration > Policies & rules > Threat policies |
| 3 | Select TABL | Tenant Allow/Block Lists under Rules |
| 4 | Add sender | Click Add for Senders, enter your domain |
| 5 | Set expiration | Microsoft recommends temporary entries |
Security considerations that matter
Unlike IP allow lists, TABL entries still scan for malware and high-confidence phishing. However, when adding a sender to the Allow list, you’ll need to submit a copy of the email message to the Microsoft team for review (they want to see what you’re sending before giving you special privileges).
Alternative approaches for smaller needs
For smaller implementations, customers can add your sending address to their Outlook safe sender’s list or create inbox rules. While less comprehensive than TABL, the method works well for specific sender-recipient relationships.
Always emphasize to customers that allowlisting should be temporary whenever possible. As your sender reputation improves through proper practices, the need for manual overrides decreases significantly.
Which Office 365 spam filter settings impact delivery?
Microsoft provides granular controls that administrators can adjust to fine-tune their spam filtering behavior.
Policy hierarchy complications
Settings in the default or custom anti-spam policies get ignored if a recipient is also included in the Standard or Strict preset security policies. Many enterprise customers use these preset policies, which override custom allowlisting attempts.
When customers report that allowlisting “doesn’t work,” they may be running preset security policies that take precedence over custom rules.
Connection filter controls
Administrators can access connection filters through Security & Compliance Center > Threat management > Policy > Connection filter. These settings determine which IP addresses bypass initial filtering checks.
Advanced spam filtering nuances
The Test mode settings, the Increase spam score settings, and most of the Mark as spam settings are part of Advanced Spam Filtering (ASF) in anti-spam policies. These granular controls can impact your messages even when basic spam filtering passes.
| ASF Setting | Common Trigger | Impact |
| Image links to remote sites | Email tracking pixels | High spam score |
| Empty messages | Image-only emails | Filtering |
| JavaScript/ActiveX | HTML complexity | Block/quarantine |
| Numeric IP URLs | Poor link practices | Spam verdict |
| URL shorteners | Shortened links | Score increase |
How do you read Microsoft 365 spam headers?
Header analysis gives you concrete data about why messages hit junk folders instead of relying on guesswork (because playing email detective beats playing email roulette) — these diagnostic details reveal exactly what triggered spam filtering decisions.
Key diagnostic headers to examine
During message inspection for malware and spam, EOP generates SCL for each message that indicates the probability of spam classification. EOP also adds multiple headers to the message throughout the transport pipeline.
| Header | Information | Purpose |
| X-Microsoft-Antispam | BCL score and bulk detection | Bulk assessment |
| X-Forefront-Antispam-Report | SCL, auth results, policy actions | Primary diagnosis |
| Authentication-Results | SPF, DKIM, DMARC status | Auth verification |
| X-MS-Exchange-Organization-SCL | Final confidence level | Delivery decision |
Authentication result interpretation
The Authentication-Results header reveals whether your technical setup passes Microsoft’s checks.
Look for “pass” verdicts on SPF, DKIM, and DMARC. Failed authentication significantly increases spam scoring.
BCL troubleshooting insights that help
BCL and SCL get affected by various factors, including user engagement, email engagement, data volume surges, irregular sending patterns, and low email engagement rates.
When you see consistently high BCL scores (7+), focus on list quality and engagement improvement rather than content changes. Microsoft’s algorithms have identified your sending patterns as generating complaints, which requires reputation repair rather than message tweaks.
Sample header analysis:
- X-Microsoft-Antispam: BCL:7;
- X-Forefront-Antispam-Report: SCL:6;IPV:NLI;
- Authentication-Results: spf=pass; dkim=pass; dmarc=pass;
The combination above shows authentication passed, but bulk characteristics triggered spam folder delivery. The solution involves improving engagement metrics and list quality rather than technical fixes.
What about SPF bypass in Office 365?
SPF bypassing requires careful consideration since it affects domain-level authentication signals that Microsoft uses for reputation scoring (think of SPF as your email’s passport — bypassing it raises red flags at every checkpoint).
When bypass makes legitimate sense
Organizations using third-party email services or routing through security appliances may need SPF accommodation. However, complete SPF bypassing creates authentication gaps that hurt long-term deliverability.
Connection filter approach
Instead of disabling SPF entirely, create connection filters that recognize your legitimate email sources. Navigate to Microsoft 365 Defender portal > Email & collaboration > Policies & rules > Threat policies > Anti-spam > Connection filter policy.
Add your email service provider’s IP ranges to the “Always allow messages from the following IP addresses or address range” list. Your approach maintains SPF validation while accommodating your email infrastructure.
Enhanced filtering solution
Enhanced filtering for connectors provides the recommended solution (Microsoft actually prefers you use the method they built rather than work around it). Enhanced filtering won’t break authentication signals such as SPF, DMARC, and DKIM.
Enhanced filtering tells Microsoft which IP addresses are part of your legitimate email flow, allowing proper authentication validation while bypassing initial connection blocks.
How can you turn off junk mail filtering safely?
Complete junk mail filtering disabling isn’t possible or advisable, but you can adjust filtering sensitivity for specific scenarios.
Microsoft’s stance remains clear about maintaining security protections (they’re not going to let you turn off their entire spam protection system).
Filtering limitations that exist
You can’t completely turn off spam filtering in Microsoft 365, but you can use Exchange mail flow rules (also known as transport rules) to bypass most spam filtering on incoming messages. Complete disabling would expose organizations to significant security risks.
| Policy type | Default BCL threshold | Recommended adjustment |
| Default anti-spam | 7 | Raise to 8-9 for less filtering |
| Standard preset | 6 | Policy-level changes required |
| Strict preset | 5 | Not recommended to modify |
Raising BCL thresholds from 7 to 8 or 9 reduces bulk email filtering while maintaining protection against obvious spam.
User-level controls available
End users can manage their junk email settings through Outlook’s junk email options.
However, administrative policies often override individual user preferences, particularly in enterprise environments with strict security requirements (your IT department’s rules trump your personal preferences).
What’s the ultimate solution for Office 365 deliverability?
Sustainable Microsoft 365 deliverability requires a systematic approach that builds genuine trust signals over time rather than relying on bypass tricks (because tricks eventually stop working when algorithms get smarter).
Email warmup foundation
Improving your email deliverability takes considerable time, and you may need to adjust your practices over time.
Automated email warmup services gradually increase sending volume while maintaining engagement patterns that Microsoft’s algorithms recognize as legitimate business communication.
The process typically takes 8-12 weeks to build a sufficient reputation for consistent inbox delivery.
Authentication across all touchpoints
Every subdomain, email service, and sending tool must properly configure SPF, DKIM, and DMARC records. Inconsistencies in authentication create reputation gaps that Microsoft’s systems flag as suspicious.
List hygiene importance
Make sure your email list is clean and up-to-date. Communication with suspicious users can also degrade your sender’s reputation. Regular validation removes inactive addresses that contribute to negative reputation signals.
Continuous monitoring approach
Header analysis, reputation monitoring, and engagement tracking help identify issues before they impact entire campaigns. Active management prevents the reputation damage that requires lengthy recovery periods.
Your deliverability solution starts here
Office 365 deliverability challenges require expertise, time, and systematic implementation across multiple technical areas.
While the strategies outlined above work effectively, executing them while managing your core business responsibilities can overwhelm even experienced teams (you’ve got a business to run, not a spam filter to debug).
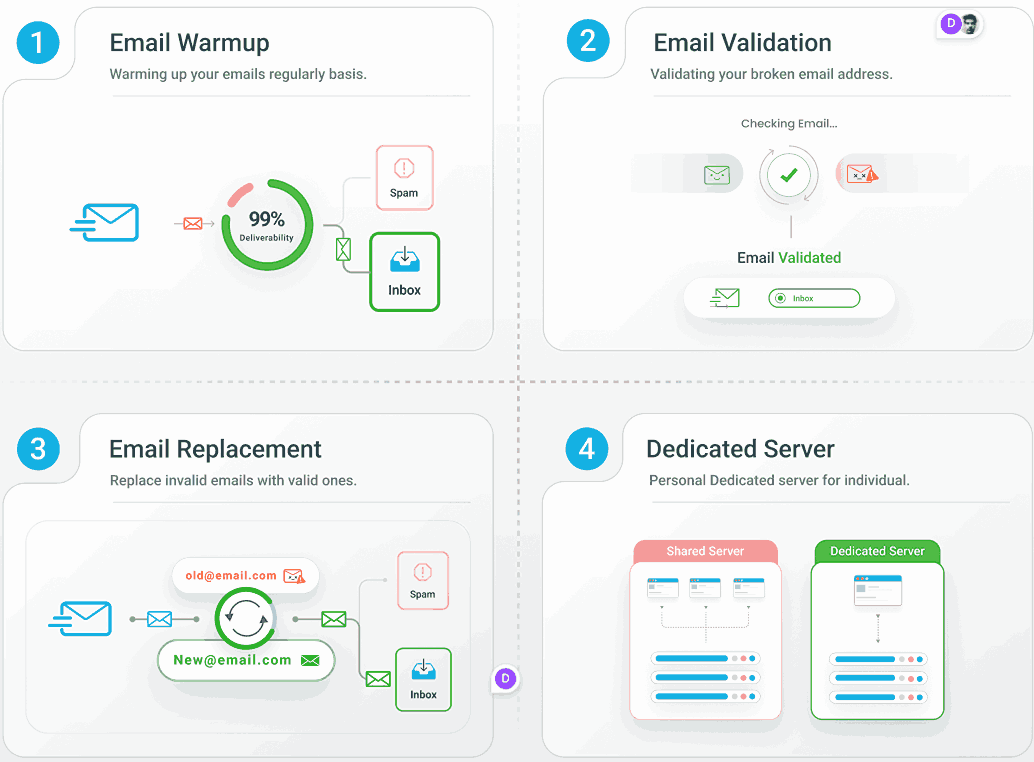
EmailWarmup.com handles the entire process for you:
- Dedicated IP management for reputation control
- Ongoing deliverability monitoring and improvement
- Expert analysis of your current Microsoft 365 delivery issues
- Customer allowlisting playbooks using secure TABL methods
- 8-12 week reputation building through intelligent email warmup
- Complete authentication setup and monitoring across all domains
- List validation and automatic replacement for optimal engagement
We’ve helped hundreds of B2B SaaS companies transform their Microsoft 365 delivery rates from junk folder disasters to consistent inbox placement. Let us handle the technical complexity while you focus on growing your business.
Schedule a free consultation today
No, a complete bypass isn’t possible and would create significant security vulnerabilities. We recommend that you don’t use these features because they may override Microsoft 365 spam filter verdicts. Focus on building legitimate trust signals through proper authentication and gradual reputation improvement.
SCL (Spam Confidence Level) measures overall spam likelihood from -1 to 9, while BCL (Bulk Complaint Level) assesses commercial email complaint risk. A BCL greater than the threshold converts to SCL 6, triggering spam verdict actions.
Email warmup typically requires 8-12 weeks to establish a sufficient reputation for consistent Microsoft 365 inbox delivery. Rushing the process by increasing volume too quickly can trigger spam filters and extend recovery time.
IP allowlisting creates security risks by bypassing authentication checks and spam filtering. Entries in allowed lists create a high risk of attackers successfully delivering filtered email to inboxes. Recommend TABL entries instead, which maintain security protections.
Authentication success doesn’t guarantee inbox delivery. Microsoft considers sender reputation, engagement patterns, list quality, and content characteristics alongside authentication status. Poor bulk practices trigger junk folder delivery even with a perfect authentication setup.
Outlook add-on email spam filters work alongside (not instead of) Microsoft’s built-in Exchange Online Protection. In all organizations with cloud mailboxes, email messages get automatically protected against spam. Focus on working with Microsoft’s native filtering rather than adding complexity through third-party add-ons.


