
Your phone buzzes with angry customer tickets. “I can’t reset my password!” Meanwhile, your CEO is asking why emails stopped working and revenue is dropping.
You’ve discovered your domain has been blacklisted. Every minute means more frustrated customers and pressure to fix this immediately.
Getting off an email blacklist is entirely achievable when you follow the right process.
As an email deliverability consultant who has helped hundreds of businesses recover from these nightmares, I’ve prepped this comprehensive guide that covers:
- Step-by-step delisting procedures for major blacklists
- Instant blacklist detection and identification methods
- Evidence gathering and removal request strategies
- Timeline expectations and monitoring setup
- Root cause analysis to prevent re-listing
Let’s help you escape all the dreaded blacklists your email has fallen into, and boost your sender’s reputation again.
Quick reference — your blacklist recovery roadmap
Don’t have the time to read the entire piece? No worries. Here’s a quick skim:
| Blacklist type | Identification method | Delisting process | Expected timeline |
| EmailWarmup.com | Automated monitoring | Tried and tested delisting procedure | 24-48 hours |
| Spamhaus (SBL/CSS/XBL) | MXToolbox, bounce messages | Online removal form plus evidence | 24-72 hours |
| Barracuda | Barracuda lookup tool | Email request with documentation | 1-3 business days |
| Microsoft/Outlook | Postmaster Tools, SNDS | Dedicated delisting portal | 24-48 hours |
| SURBL/URIBL | Domain reputation tools | Contact form submission | 2-7 days |
| UCEPROTECT | UCEPROTECT checker | Hosting provider involvement | 1-7 days |
When blacklists have you cornered, we’re your escape route
You could spend days learning removal procedures for dozens of different blacklists, or you could let the experts handle it while you focus on damage control.
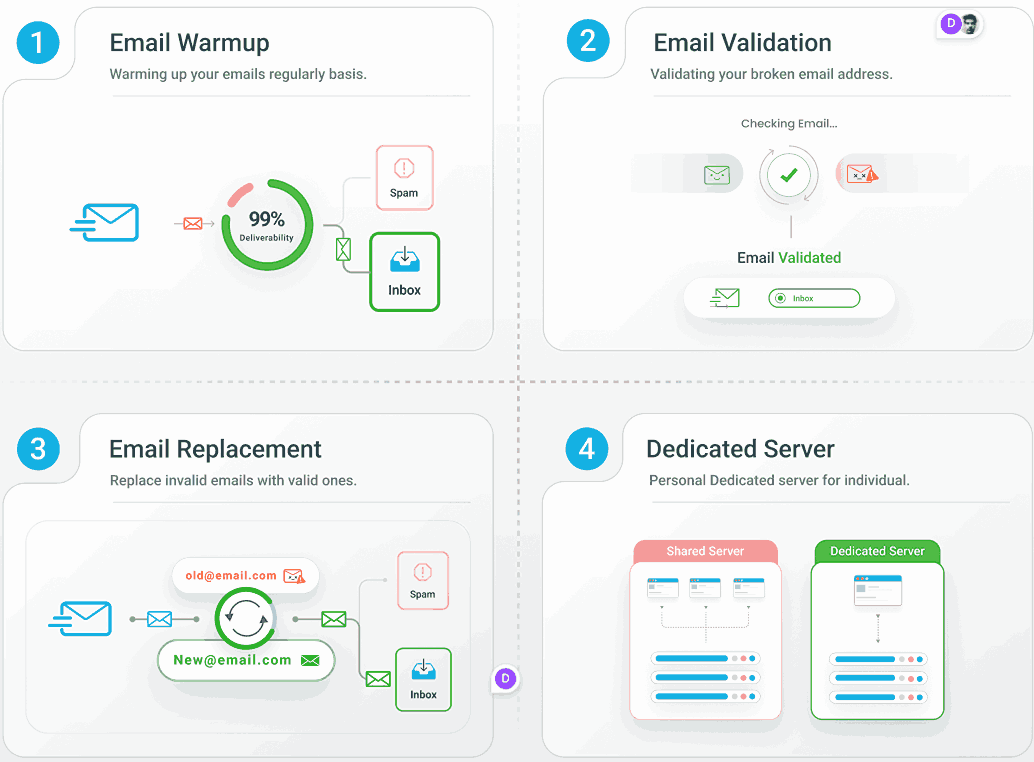
EmailWarmup.com specializes in emergency blacklist recovery because we know every hour counts when your customers can’t receive critical emails.
Our deliverability consultants have seen every type of blacklist scenario and know exactly which buttons to push for the fastest removal.
- Direct relationships with major blacklist administrators for faster processing
- Complete evidence packages that prove you’ve fixed the underlying issues
- Pre-written removal templates that blacklist operators actually approve
- Emergency blacklist scanning across 200+ databases within minutes
- Real-time monitoring that catches new listings before they spread
- 24/7 support because blacklists don’t respect business hours
We offer a free, unlimited email deliverability checker that helps you identify your exact blacklist status and submit removal requests within the hour.
Schedule your emergency consultation call
How do you identify which blacklist has you trapped?
Before you can escape an email blacklist, you need to know exactly where to look and why it happened. Understanding the specific reason for your blacklisting determines your entire recovery strategy.
Reading bounce-back messages for clues
When your emails get rejected, bounce-back messages often contain valuable information about which blacklist has flagged you. Smart email administrators learn to read these messages like a roadmap back to deliverability.
Common bounce message patterns reveal specific blacklists. “550 5.7.1 Service unavailable; Client host [IP] blocked” typically indicates a Spamhaus listing, while “421 4.7.1 Service temporarily unavailable” often points to temporary reputation issues.
“550 SC-001” suggests Barracuda blocking, and “550 5.7.606 Access denied, banned sending IP” indicates Microsoft blocking.
Keep copies of these bounce messages because you’ll need them for your removal requests. Many messages include direct links to the blacklist provider’s lookup tools, making your detective work significantly easier.
Essential blacklist checking tools
Several powerful tools can scan your IP address, domain, or email against hundreds of blacklists simultaneously. The key is using multiple tools since each one checks different databases.

- EmailWarmup.com (comprehensive blacklist checking + removal)
- MXToolbox Blacklist Check (scans 100+ major blacklists)
- Spamhaus Lookup (SBL, CSS, XBL, PBL databases)
- Google Postmaster Tools (Gmail-specific insights)
- Sender Score by Validity (reputation scoring)
- DNSBL.info (real-time blacklist monitoring)
- MultiRBL.valli.org (Multi-blacklist checker)
- Microsoft SNDS (Outlook delivery data)
Most developers make the mistake of checking only one or two tools when comprehensive scanning reveals the full scope of their blacklist problem.
Unless you’re working with a dedicated deliverability-first tool like EmailWarmup.com, it’s really difficult to rely on one tool for accuracy.
Also, manually checking dozens of blacklists every day isn’t just time-consuming (it’s practically impossible when you’re dealing with a crisis). Emergency situations require emergency tools that work around the clock.
EmailWarmup.com continuously monitors over 200 blacklist databases, providing instant alerts the moment your IP or domain gets listed anywhere. We don’t just tell you that you’re blacklisted. We tell you why, giving you the exact evidence needed for successful delisting requests.
That way, you don’t have to worry about checking for email blacklists while the experts take care of it.
Warning signs in your email metrics
Sometimes the first indication of blacklisting comes from your email analytics before you even realize there’s a problem. Smart monitoring catches issues before they become full-blown crises that require emergency intervention.
| Metric | Normal range | Blacklist warning sign |
| Open Rate | 20-35% | Below 5% |
| Bounce Rate | Under 2% | Above 2% consistently |
| Spam Complaints | Under 0.1% | Above 0.1% |
| Click-Through Rate | 2-5% | Dramatic decrease |
| Soft Bounces | Under 5% | Increasing trend |
Your email service provider’s dashboard usually shows these metrics clearly. Set up alerts for sudden changes because catching blacklisting early makes removal much faster.
What causes email blacklisting in the first place?
Getting delisted without fixing the underlying problem is like getting out of jail just to commit the same crime again. Blacklist providers won’t even consider removal requests unless you can prove the root cause has been addressed.
Understanding why your email got blacklisted helps you gather the right evidence for removal requests. More importantly, it prevents the same thing from happening again (which would be even more embarrassing to explain to your CEO).
High spam complaint rates
When recipients mark your emails as spam, it signals to ISPs that your content is unwanted. Anything above 0.1% is dangerous territory. That’s just 1 complaint per 1,000 emails sent.
Spam complaints usually happen when email lists contain non-subscribers, content feels irrelevant or overly promotional, unsubscribe processes are hidden or complicated, or email frequency overwhelms recipients.
The tricky part about spam complaints is that they’re often delayed. Someone might mark your email as spam days after receiving it.
Poor list hygiene and spam traps
Poor email list hygiene creates a domino effect of problems that eventually leads to blacklisting. Email providers watch bounce rates carefully as an indicator of sender quality.
- Invalid addresses that generate hard bounces
- Old addresses that get converted into spam traps
- High bounce rates that signal poor list management
- Purchased lists containing honeypot addresses designed to catch spammers
Spam traps are particularly dangerous because they’re designed to catch senders who don’t follow proper list-building practices. Hit a spam trap, and you’re almost guaranteed to get blacklisted.
Missing email authentication
Without proper SPF, DKIM, and DMARC records, your emails appear suspicious to receiving servers. Authentication protocols act like a digital passport, proving your emails are legitimate.
| Protocol | Purpose | What it does |
| SPF | Server Authorization | Authorizes which servers can send from your domain |
| DKIM | Email Signatures | Provides cryptographic signatures proving authenticity |
| DMARC | Policy Instructions | Tells receivers what to do with unauthenticated emails |
Many IT teams think authentication is optional — it’s not.
Missing these records makes you look like a spammer even when you’re sending legitimate emails.
Volume spikes and suspicious sending patterns
Sudden changes in email volume trigger spam filters designed to detect compromised accounts. Email providers expect consistent, predictable sending patterns from legitimate businesses.
Red flag sending behaviors include sending 10,000 emails when your usual volume is 500, bulk sending during unusual hours like 3 AM, rapid-fire sending without proper pacing, and using new IP addresses without proper email warmup.
The algorithms watching for these patterns are incredibly sensitive. Even doubling your normal send volume can trigger suspicion if you haven’t warmed up your reputation properly.
Compromised accounts or servers
If hackers gain access to your email systems, they’ll use them to send spam, malware, or phishing emails. Unfortunately, you’re responsible for everything sent from your infrastructure, even if you didn’t send it.
Security vulnerabilities that lead to compromise include weak passwords on email accounts, outdated server software with security vulnerabilities, a lack of two-factor authentication, and a lack of monitoring for suspicious login activity.
Compromised account blacklisting is particularly frustrating because you’re essentially being punished for being a victim. However, blacklist providers don’t care about excuses. They care about results.
How do you fix the problems before requesting removal?
Attempting delisting without addressing root causes is like trying to bail water from a sinking ship without plugging the holes. Most blacklist providers require proof of corrective actions before processing removal requests.
The key is demonstrating that you’ve not only identified the problem but taken concrete steps to prevent it from happening again. Documentation of these fixes becomes crucial evidence for your removal requests.
Setting up email authentication
Email authentication is non-negotiable for long-term deliverability success. These protocols prove your emails are legitimate and haven’t been tampered with during transit.
SPF records tell receiving servers which IP addresses are authorized to send emails from your domain. Without them, your emails look suspicious to receiving servers. A typical SPF record looks like:
v=spf1 include:_spf.google.com include:sendgrid.net ~all.DKIM adds a cryptographic signature to your emails, allowing receivers to verify they haven’t been tampered with during transit. Your email service provider usually handles the technical setup.
Still, you need to coordinate carefully between your IT team and email service provider (because configuration mistakes can actually make deliverability worse).
DMARC tells receivers what to do when emails fail SPF or DKIM checks. A typical DMARC policy looks like:
v=DMARC1; p=quarantine; rua=mailto:dmarc@yourdomain.com; pct=100. DMARC also provides valuable reporting on authentication failures that helps you monitor ongoing reputation health.
Security improvements
If compromised accounts caused your blacklisting, security improvements are mandatory before any blacklist provider will consider removal. You need to prove the vulnerability has been closed.
- Install security patches on email servers
- Implement IP whitelisting for admin access
- Set up monitoring for unusual login attempts
- Enable two-factor authentication on all email accounts
- Update all passwords to complex, unique combinations
Document every security improvement you make. Blacklist operators want to see evidence that you’ve taken the threat seriously and implemented proper safeguards.
List cleaning and content optimization
Your email list is only as strong as its weakest subscriber — removing problematic addresses is essential for reputation recovery.
Immediate removals include hard bounces (invalid addresses), spam trap hits (honeypot addresses), abuse complaints and unsubscribes, and inactive subscribers with no engagement in 6+ months.
Email verification tools like EmailWarmup.com’s email validation API, ZeroBounce, EmailListVerify, NeverBounce, and Mailtrap help identify problematic addresses before they cause problems.
If you don’t want to lose your precious leads while validating your lists, you can go for EmailWarmup.com, which not only removes bad addresses from your list but also replaces them with correct ones.
Moreover, list cleaning isn’t a one-time activity. Successful email programs include ongoing list hygiene as part of regular maintenance because email addresses go bad constantly.
Another important aspect is your content. Content optimization requires a balance between avoiding spam triggers and maintaining effectiveness for your business goals.
Maintain a healthy text-to-image ratio (at least 60% text), avoid excessive capitalization and exclamation points, include clear sender identification and contact information, provide easy unsubscribe options, and personalize content based on subscriber preferences.
You can also check if there are any spammy elements in your content via our free email spam checker.
What’s the step-by-step removal process for major blacklists?
Each blacklist provider has its own delisting process, requirements, and timeline. Submitting incomplete or incorrect information can delay removal or result in rejection.
The removal process varies dramatically between providers. Some are automated and fast, while others require manual review and extensive documentation.
Spamhaus removal procedures
Spamhaus operates the most widely used blacklists globally, making their removal process critical to understand. They’re also known for being thorough in their review process.
Visit the Spamhaus Blocklist Removal Center and enter your IP address or domain for lookup. If listed, click the removal request link and provide a detailed explanation of corrective actions taken.
Include evidence of security improvements like screenshots of authentication record updates, documentation of compromised account securing, list cleaning reports showing removed addresses, and security audit results.
The timeline is typically 24-72 hours for legitimate requests. Spamhaus doesn’t just rubber-stamp removal requests. They actually review the evidence you provide and may ask follow-up questions.
Barracuda delisting process
Barracuda’s process requires more detailed documentation than most other blacklists. They want to understand exactly what went wrong and how you fixed it.
Use the Barracuda Lookup tool to confirm listing, then email your removal request to barracudacentral@barracuda.com. Include full headers of bounced messages, provide network diagrams showing email infrastructure, and document all corrective actions taken.
Barracuda often asks technical questions about your infrastructure, so having detailed documentation ready speeds up the process significantly. The timeline typically runs 1-3 business days.
Microsoft and Outlook delisting
Microsoft’s delisting process is streamlined through its sender support portal. They’ve made it relatively user-friendly compared to other providers.
- Access Microsoft’s sender support portal
- Submit IP address and domain information
- Provide sample bounced message headers
- Complete sender information questionnaire
- Upload evidence of authentication setup
Microsoft is generally faster than other providers with 24-48 hour timelines. However, they’re also strict about repeat offenses. Getting blacklisted again by Microsoft becomes progressively harder to resolve.
Writing removal requests that get approved
Your delisting request should tell a story of recognition, responsibility, and resolution. Blacklist operators want to see that you understand what went wrong and have taken concrete steps to fix it.
Structure your request to acknowledge the listing and take responsibility, explain how you identified the root cause, detail specific corrective actions taken, outline measures to prevent recurrence, and attach supporting documentation.
The tone should be professional and factual. Emotional appeals or aggressive language typically backfire with blacklist operators.
A sample request excerpt might read:
“We discovered our IP address 192.168.1.100 was compromised on [date] due to a weak password on our admin account. We immediately secured the account, updated all passwords, enabled 2FA, and implemented IP whitelisting. Attached are our new SPF/DKIM records and security audit results.”
Documentation that gets results
Blacklist operators want proof, not promises. The quality of your supporting documentation often determines whether your removal request gets approved.
Include before/after screenshots of authentication records, email server log excerpts showing security improvements, list cleaning reports with statistics, network security scan results, and monitoring setup confirmations.
Organize your documentation clearly and label everything. Blacklist operators review dozens of requests daily, so making their job easier makes your approval more likely.
How long does blacklist removal actually take?
Understanding realistic timelines helps manage expectations and plan alternative communication strategies during the delisting process. Knowing what to expect prevents panic when removal takes longer than hoped.
Timeline expectations vary dramatically based on the blacklist provider, the severity of the violation, and the quality of your removal request. Some removals happen in hours, others take weeks, depending on complexity.
Fast track removals
Fast removals typically happen within 24-48 hours for straightforward cases. Microsoft/Outlook delisting, Google/Gmail reputation recovery, automatic removals from behavior-based lists, and first-time offenses with clear documentation usually fall into the category.
Fast removals typically happen when the blacklisting was caused by a clear, one-time incident that’s been thoroughly addressed. Providers can quickly verify the fix and approve removal.
Standard processing timeline
Most removals fall into the 3-7 day category for Spamhaus manual review cases, Barracuda BRBL removal, SURBL/URIBL domain delisting, and most commercial blacklist providers.
Standard processing involves manual review of your documentation and evidence. The timeline depends on the provider’s current workload and case complexity.
Extended timeline scenarios
Some cases take 1-2 weeks or more for UCEPROTECT Level 3 (requires hosting provider involvement), repeat offender cases requiring additional scrutiny, complex compromise cases with extensive evidence review, and cases where initial documentation was insufficient.
Extended timelines usually indicate either a serious violation or problems with your initial removal request. Don’t panic — use the extra time to strengthen your case.
What to do while waiting for removal
Don’t sit idle while your delisting request is processed. Use the waiting time productively to minimize business impact and prepare for post-removal monitoring.
- Monitor for additional blacklist listings
- Track email metrics for improvement signs
- Check delisting status daily using lookup tools
- Monitor bounce rates and delivery metrics closely
- Prepare post-removal reputation rebuilding strategies
- Set up an alternative sending infrastructure if possible
- Communicate with customers about potential email delays
- Prepare backup communication channels (SMS, phone calls)
When removal requests get denied
Sometimes removal requests get rejected, which feels devastating when you’re already dealing with delivery problems. However, denials usually include specific feedback that helps you strengthen your next attempt.
Common denial reasons include insufficient evidence of corrective actions, ongoing spam complaints or bounces, incomplete or unclear documentation, and repeat violations within short timeframes.
Request specific feedback on denial reasons, address all identified deficiencies, wait the recommended time period before resubmitting, consider escalating to senior technical contacts, and seek professional deliverability consultation.
Denials are frustrating but rarely permanent. Most legitimate businesses eventually get removed when they provide adequate documentation and evidence of fixes.
Ready to reclaim your email reputation?
Getting off an email blacklist doesn’t have to be a solo mission fraught with uncertainty and stress.
While the process is manageable when you know the right steps, it’s also time-sensitive and technically demanding (especially when your business revenue is on the line).
Hundreds of developers and marketers trust EmailWarmup.com to handle their deliverability crises and ongoing reputation management.
- Complete authentication setup with ongoing monitoring
- Expert-written delisting requests that get approved faster
- 24/7 blacklist monitoring across 200+ databases with instant alerts
- Advanced warmup strategies that prevent future blacklisting incidents
- Automated evidence gathering and documentation for removal requests
- Dedicated deliverability consultants who handle the technical heavy lifting
Our deliverability experts have successfully recovered sender reputations for companies just like yours, often achieving delisting within 24-48 hours instead of weeks.
Schedule your free consultation call
Frequently asked questions
Here are some commonly asked questions on this topic:
Yes. Prevention requires proper email authentication, clean email lists, continuous monitoring, and following email marketing regulations. Most repeat blacklisting happens because businesses didn’t address root causes properly the first time.
Multiple listings often indicate serious underlying issues like compromised servers. Submit separate removal requests to each provider since they operate independently. Priority should go to the most impactful blacklists first.
Switching ESPs won’t automatically solve blacklisting problems because reputation is tied to your domain and IP address, not your service provider. However, moving to a dedicated IP might help if you’re using a compromised shared IP.
Most blacklist providers send confirmation emails when your removal request is processed. Test using the same lookup tools you used initially to confirm your IP or domain no longer appears.
Hard bounces are permanent rejections (invalid addresses), while soft bounces are temporary issues (full mailboxes). Hard bounces are more dangerous for blacklisting because they indicate poor list hygiene.


