
Email spam filtering calculates probability scores by analyzing dozens of characteristics across sender identity, content quality, routing paths, and recipient behavior. When that score crosses the threshold, your campaign vanishes.
As an email deliverability consultant who has rescued hundreds of campaigns from spam folders, I’ve prepared this guide covering:
- Practical bypass strategies that work
- Actions filters take on flagged messages
- Specific criteria triggering filtering systems
- Detection techniques from rule-based to AI-powered
- Multi-layered filtering mechanisms that assign spam scores
Testing across 15 major providers reveals 83.1% average inbox placement — meaning one in six emails fails entirely (with 10.5% hitting spam and 6.4% vanishing completely). Understanding filter mechanics separates inbox placement from invisibility.
TLDR: Quick skim for email spam filtering
Here’s email filtering at a glance:
| Mechanism | What it checks | Impact |
| Authentication | SPF, DKIM, DMARC verification | Critical (missing = automatic filtering) |
| Content analysis | Suspicious words, formatting, and links | Moderate (contributes to score) |
| Header inspection | Routing path, IP location, DNS | High (detects spoofing) |
| Reputation scoring | Domain/IP history, engagement rates | Critical (past predicts future) |
| Behavioral signals | Opens, replies, complaint rates | High (users train filters) |
| AI/ML classification | Pattern recognition, anomaly detection | Growing (adapts to threats) |
How does email spam filtering work?
Filters operate on probability, not absolutes, because single characteristics rarely prove spam status definitively. Each signal adds to or subtracts from your score — when that total exceeds the threshold, action happens. Paul Graham’s foundational work explains perfectly:
“Statistical filters look at the entire contents of each incoming email and decide whether it’s spam based on its overall similarity to previous spam.”
Modern systems layer multiple techniques simultaneously. Content filters scan message text while reputation filters check your domain against spam databases. Authentication protocols verify you’re authorized to send, while behavioral analysis watches how recipients interact over time — none work alone anymore.
Wild. A message might pass content checks but fail authentication. Another might have a perfect setup but a terrible engagement history (which matters more than senders realize). The combination determines your fate.
What criteria trigger spam filters?
Filters evaluate four major categories, each carrying a different weight in calculating your final score.
Sender authentication
Authentication protocols verify your identity. SPF identifies authorized servers, DKIM uses cryptographic signatures to confirm message integrity, and DMARC ties them together, instructing receiving servers on what to do when checks fail.

Microsoft’s May 2025 enforcement made authentication mandatory for bulk senders (>5,000 daily emails). Non-compliant messages get rejected with error code “550 5.7.515 Access denied” — no junk folder, no delivery. Gmail and Yahoo enforce similar requirements.
Domain and IP reputation compounds technical checks. Addresses previously linked to spam get flagged instantly, high sending rates from unknown sources trigger suspicion, and blocklist placement permanently damages inbox ability.
Content signals
Content analysis evolved beyond keyword matching. Filters won’t automatically block “free” or “limited time” offers anymore, but a heavy concentration of marketing language still signals promotional intent.
What actually triggers filters:
- Foreign characters in English emails
- Image-only messages with minimal text
- Shortened URLs or excessive link density
- Grammar mistakes (though AI-generated spam reduced this signal’s reliability)
- Excessive capitalization and punctuation
- Malware-associated attachment types
Research shows no single algorithm performs best across all datasets — successful filtering requires combining multiple approaches with strong feature engineering.
Header metadata
Headers contain routing information invisible to recipients but critical for filters because every email creates a “chain of custody” through servers that gets examined for anomalies.
| Suspicious pattern | What it reveals |
| Broken routing sequences | Expected server hops are missing |
| Geographic mismatches | Claimed location ≠ actual originating IP |
| DNS inconsistencies | IP addresses don’t map to domain names |
| Source spoofing | Gmail messages not from Gmail servers |
Filters cross-reference metadata against authentication records. Your SPF claims certain servers can send for your domain, but your message originated elsewhere? Strike. Display name shows “john@company.com,” but the actual address is “randomstring@suspiciousdomain.ru”? Another strike.
User behavior
Engagement metrics increasingly determine deliverability because recipients reveal preferences better than algorithms ever could.
When users consistently open, read, reply to, or forward messages, future emails get preferential treatment. When they delete without opening, mark as spam, or ignore messages for months, filters downgrade reputation.

Gmail emphasizes behavioral signals heavily — analyzing how users interact with similar emails across millions of mailboxes. If your industry, sending pattern, or content matches messages people frequently ignore or report, deliverability suffers even with perfect authentication.
Complaint rates must stay below 0.3% for bulk sender requirements. Most experts recommend targeting under 0.1% because just three complaints per thousand emails can trigger domain-wide filtering.
Which detection techniques does email spam filtering uses?
Different methods work together to catch evolving tactics because spammers constantly adapt. We call this the Layered Defense approach — combining multiple detection systems so bypassing one doesn’t guarantee delivery.
Rule-based systems
Rule-based filters apply specific criteria that administrators define. Microsoft Outlook’s “rules” feature exemplifies this — blocking certain attachment types, flagging messages with particular content patterns, or routing based on sender characteristics.
These work well for known threats but struggle with novel tactics because spammers change addresses, domains, and phrasing faster than rules can be updated. That’s why rule-based filtering alone fails spectacularly against modern campaigns.
Bayesian email spam filtering
Bayesian filters learn from examples rather than following predefined rules. They analyze messages you mark as spam versus legitimate mail, building statistical models of spam characteristics specific to you.
The TREC Spam Track framework established benchmarks for testing filters chronologically — preventing artificially inflated accuracy from training on future examples (which would be like studying the test before taking it).
Training accuracy improves with consistency. The more you mark spam as spam and legitimate mail as not spam, the more accurate your personal filter becomes. Corporate filters aggregate feedback across thousands of users to improve detection globally.
AI/ML detection
Machine learning transformed filtering by identifying subtle patterns humans miss. Instead of checking explicit rules or word frequencies, AI analyzes relationships, context, and behavior across massive datasets.
Advanced email spam filtering flags emails based on relationship analysis — messages from unknown vendors sent generically to multiple company employees get scored as suspicious. Systems develop usage profiles for each user (tracking typical relationships, tone, link-sharing patterns) to detect deviations suggesting account compromise.
Nope. AI-powered phishing surged 466% in Q1 2025. Generative AI eliminates the grammar mistakes and awkward phrasing that previously signaled phishing — modern attacks look linguistically perfect. Detection systems must employ equally sophisticated AI to counter these threats.
The catch is that AI requires massive training datasets and computational resources. Small businesses can’t build custom models, so talking to an email deliverability consultant is necessary.
Real-time analysis
Modern filters inspect messages dynamically. URL analysis systems actively visit links in isolated environments (sandboxing) to observe behavior before delivering messages — catching zero-day phishing sites not on blocklists yet.
Greylisting temporarily rejects emails from unknown senders, instructing servers to retry later. Legitimate mail servers retry automatically, while spam botnets (which rarely retry) get filtered out.
Challenge-response systems send verification requests back to senders — humans pass, automated systems fail.
What happens to filtered emails?
Once your message exceeds the spam threshold, several outcomes become possible based on provider policies and flag severity.
| Action | What happens | When it’s used |
| SMTP rejection | Refused during initial connection (5xx error) | Missing authentication, severe reputation damage |
| Quarantine | Held in a secure area for admin review (1-30 days) | High-confidence phishing, suspicious patterns |
| Spam routing | Delivered but sorted away from the primary inbox | Most common — 10.5% average |
| Subject tagging | “[SPAM]” prepended before delivery | SpamAssassin and similar systems |
| Silent deletion | Removed without trace or bounce | Admin-configured aggressive policies |
User actions feed back into systems. When recipients mark your emails as spam, filters learn messages matching your characteristics warrant filtering.
When they mark filtered messages as “not spam,” systems adjust to reduce false positives. Your sender reputation evolves constantly based on how real people interact with your campaigns.
How can you avoid spam filters?
Bypass requires addressing technical configuration, content quality, list management, and engagement simultaneously because fixing one area while ignoring others produces minimal improvement.
Technical setup
Authentication forms your foundation — the non-negotiable baseline that determines whether filters even consider your message legitimate.
SPF, DMARC, and DKIM
Implement SPF records to identify authorized sending servers, configure DKIM to sign outgoing messages cryptographically, and set up DMARC policies (start with p=none for monitoring, then progress to p=quarantine or p=reject after verifying that legitimate traffic isn’t affected).
Dedicated sending domains
Use dedicated sending domains separate from your primary business domain because email deliverability issues won’t impact transactional emails or executive communications. Send newsletters from mail.company.com rather than company.com. Configure proper reverse DNS so IP addresses map correctly to domain names.
Email warmup
Automated email warmup becomes critical for new domains because generic warmup tools send obvious template emails that ESPs flag immediately (actually damaging the reputation you’re trying to build).
Quality warmup analyzes your actual campaigns and replicates them naturally — matching sending style, volume patterns, and content characteristics to build authentic engagement history.
Use an email spam checker
Want to check where your emails actually land before committing to full campaigns?
Free Email Spam Checker Extension
See exactly where your emails land (inbox, promotions, or spam) without leaving Gmail or Outlook. Get a real-time deliverability score in your compose section, and clear placement labels in your Sent folder for emails you’ve already sent. Free of cost!
Real-time deliverability score
Percentage score appears beside your compose window before you hit send.
Inbox vs. spam visibility
Instant view of what percent reached inbox vs. spam across providers.
Sent-folder placement labels
Every sent email is tagged as inbox, promotions, or spam so you actually know where your emails landed.
Unlimited & free
While other tools charge $25–$85/mo, our extension is free forever.
Content strategy
Write clear subject lines that accurately describe message content because clickbait triggers suspicion. Avoid excessive punctuation, all caps, or mystery hooks. Keep message body focused — one primary topic, one clear call to action.
Minimize link density:
- Avoid URL shorteners like bit.ly that ESPs flag instantly
- Use visible, readable URLs rather than “click here” text
- Link to reputable websites (filters check destination domains)
Balance text with images. HTML emails should contain substantial text, even if the design is image-heavy, because some filters can’t evaluate image-only messages properly. Add ALT text for accessibility and filtering, use standards-compliant HTML with inline CSS.
List management
Remove unengaged subscribers aggressively, as someone who hasn’t opened an email in six months actively harms the sender’s reputation.
Filters interpret continued sending to unresponsive addresses as spam-like behavior. Segment lists by engagement level and adjust frequency accordingly.
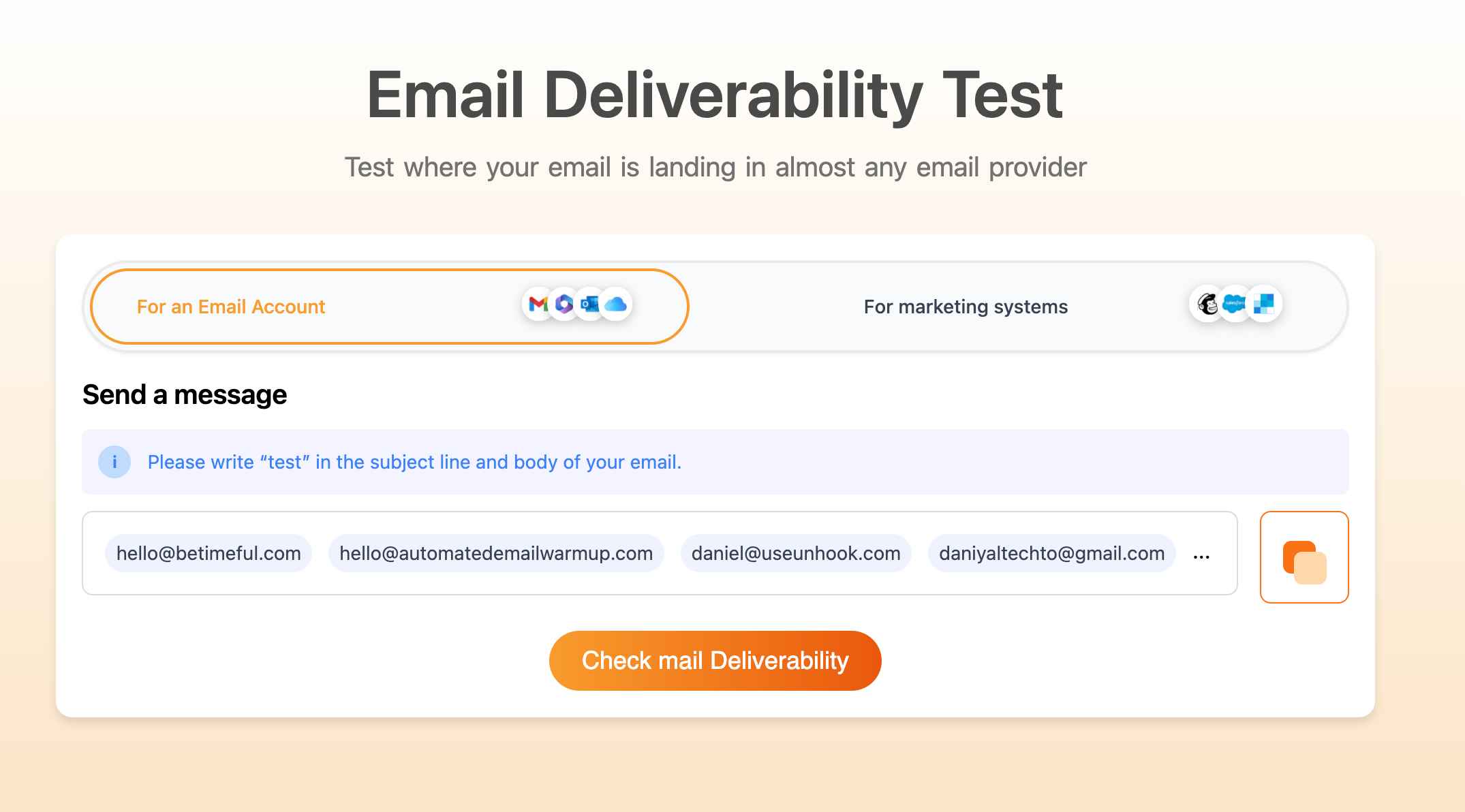
Run an email deliverability test to identify issues before they impact your campaigns. Testing across multiple providers reveals whether specific ESPs filter you more heavily (helping diagnose domain reputation issues versus content problems).
Process unsubscribe requests immediately. CAN-SPAM requires honoring opt-outs within 10 business days, but faster processing (within 24-48 hours) prevents additional complaint reports from frustrated users. Make unsubscribe links visible and functional — never require login to opt out.
Engagement optimization
Send when recipients are most likely to engage because timing affects opens, clicks, and replies.
Testing different times and days reveals patterns in your specific audience’s behavior (B2B emails often perform better on Tuesday-Thursday mornings, while B2C patterns vary by industry).
Personalize beyond inserting first names — segment campaigns by user behavior, purchase history, engagement patterns, industry characteristics, and geographic location.
Relevant messages get higher engagement, signaling value to filters. Sending generic blasts to entire lists yields poor metrics that harm email reputation.
Continuous monitoring
Track metrics beyond opens and clicks. Watch bounce rates, complaint rates, spam folder placement, and inbox versus promotions distribution because sudden changes suggest deliverability problems requiring investigation.
Monitor for email blacklists because the domain or IP appears on major lists requires immediate investigation. Delisting requires identifying and fixing the underlying problem (not just requesting removal).
Review DMARC authentication reports showing which messages pass or fail checks. Regular review catches problems like misconfigured third-party services sending on your behalf without proper SPF records.
Stop fighting filters, start fixing deliverability
EmailWarmup.com resolves deliverability issues through personalized email warm-up, mirroring your actual sending patterns (not generic templates that ESPs flag immediately), and expert guidance that identifies your specific problem areas.
Personalized email warmup
AI-guided warmups mirror your real campaigns — curated by expert copywriters to raise inbox rates.
Email spam checker
See inbox vs spam in Gmail/Outlook with our free extension and sent-folder labels for each email.
Email deliverability test
Run unlimited tests across 50+ mailbox providers with clear inbox, promotions, and spam breakdowns.
Email deliverability consultant
Free 1:1 experts who fix SPF/DKIM/DMARC, blacklist issues, segmentation without any limits, or upsells.
Email marketing consultant
Strategy, audits, and campaign optimization to grow opens, clicks, and revenue end-to-end.
Frequently asked questions
Here are some commonly asked questions about email spam filtering:
Missing authentication triggers automatic filtering regardless of content quality. Poor sender reputation from previous campaigns affects current sends, low engagement rates signal recipients don’t value your emails, and shared IP addresses get contaminated by other senders’ behavior.
Yes, but recovery requires 30-90 days of consistent effort. Implement proper authentication, remove all unengaged subscribers, reduce sending volume temporarily while focusing on engaged segments, and run continuous email warmup to rebuild positive signals. Severe cases may require switching to a new sending infrastructure entirely.
Brand new domains need 45-90 days minimum before they’re fully trusted (though you can start campaigns after 14 days of warmup). Established domains adding new infrastructure require 2-4 weeks of gradual increases. Start with 10-20 emails daily and increase by 15-20% each day. Consistency matters more than speed.
Spam filtering assumes your message is unwanted or malicious. Promotions categorization means Gmail recognizes your email as legitimate marketing delivered successfully, but sorted separately. Surveys of tab-enabled users show 51% check promotions daily — far less damaging than spam classification.
Dedicated IPs require consistent volume (minimum 50,000-100,000 monthly emails) to build a meaningful reputation because lower volumes make warming difficult. Shared IPs benefit from the provider’s established reputation but risk contamination. Most SMBs sending under 100,000 monthly should use reputable shared infrastructure.
References
- Graham, P. (2002). A plan for spam.
- Graham, P. (2003). Better Bayesian filtering.
- Cormack, G. V. (2007). TREC 2007 spam track overview.
- Radicati Group. (2024). Email statistics report, 2024-2028.
- RFC 7489. (2015). (DMARC). Internet Engineering Task Force.
- Federal Trade Commission. (2024). CAN-SPAM Act: A compliance guide for business.
- Gen Digital. (2025). Q1/2025 Gen threat report reveals AI-driven scams. PR Newswire.
- Anti-Phishing Working Group. (2024). Phishing Activity Trends Report, 4th Quarter 2024.
- Klimt, B., & Yang, Y. (2004). The Enron corpus: A new dataset for email classification research.
- Dada, E. G., Bassi, J. S., Chiroma, H., Adetunmbi, A. O., & Ajibuwa, O. E. (2019). Machine learning for email spam filtering


